The browser extension ecosystem, while convenient and useful, is also a significant and rapidly evolving threat vector in the modern IT landscape. Even in official marketplaces, malicious browser extensions can execute phishing, keylogging, spying, generalized data theft, and session hijacking attacks.
How it Works
Let’s briefly discuss how a malicious browser extension can even make it into a web store in the first place.
| Compromise Vector | Mechanism of Attack | Associated Risk |
| Malicious Update | Extension operates in a benign manner for a period and receives a malicious update pushed automatically to all users. | Broadest user base infection; high user trust makes detection difficult. |
| Developer Credential Theft | Threat actors gain unauthorized access to the developer’s web store account (e.g., via phishing). | Threat actor publishes malicious code using the legitimate developer’s verified infrastructure and trust. |
| Acquisition/Sale | Original developer sells an established extension to a third party linked to malicious monetization or surveillance. | Code is modified post-sale to insert malicious features, mostly adware or surveillance. |
| Remote Code Execution (Pre-MV3) | Malicious payload is dynamically loaded from an external server after installation. | Allows evasion of initial static code review and provides flexibility to command-and-control. |
While there are many ways to compromise a web extension, the most common method is the “malicious update” vector, where attackers submit an initially clean extension package for review by the web store. Within this package is the ability to execute remotely hosted code to execute the malicious payload, appearing benign and evading detection during initial scrutiny. In some cases, the payload execution can be controlled and modified via a remote server without needing to resubmit the package to web stores for review.
Many malicious browser extensions are initially “legitimate”, offering genuine functionality to accumulate positive reviews and even secure verification badges over a period of months or years. When an attacker decides to, they can execute the payload remotely and compromise the victims’ browser in any number of ways.
Technical Analysis
The capabilities of malicious browser extensions stems from their ability to exploit high-level APIs to perform functions that are traditionally challenging for conventional malware, such as persistent session manipulation. Below are some examples of how malicious browser extensions work.
The Rilide malware strain, first discovered in 2023, targets chromium-based browsers and often initially disguises itself as a Google Drive extension. However, distribution campaigns using PowerPoint files, X messages, and Google Ads have also been observed. Once the loader is installed, Rilide executed a script that gains full access to the victim’s browser. It takes the general path from infection to compromise:
- The loader is downloaded by the victim via one of its delivery channels, such as malvertising, social media platforms, or phishing sites. The loader is generally a PowerShell script (.ps1) disguised as something useful, like an executable file, PowerPoint presentation, or Google Drive extension.
- The loader deposits a number of files that make up the Rilide extension such as JavaScript files and
manifest.jsoninto the victim’s browser directory. The loader will often modify existing browser shortcut files (.lnk) for Chromium browsers to include the--load-extensioncommand line switch, forcing the browser to load the extension every time it is launched. - The extension contacts the command-and-control server to fetch configuration data, including a current targeted list of websites including cryptocurrency exchanges, email clients, and financial services organizations. The aforementioned JavaScript code provides the following functionality:
- The ability to inject and execute JavaScript code on webpages
- The ability to read and modify clipboard content
- The ability to access information within the active tab
- The ability to modify network requests made by the browser
- When a user visits a targeted domain, the extension injects the aforementioned JavaScript code with the following goals:
- Take constant screenshots of the user’s browser
- Create a malicious browser notification
- Return browsing history
- Fetch all cookies
- Open a tab with a given URL
- Once the desired information has been collected by the extension’s service worker, it is sent back to the attacker’s command-and-control server.
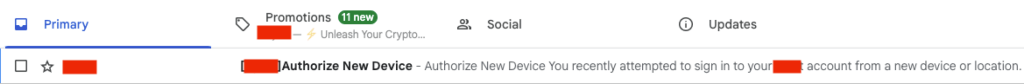
Rilide contains a number of other supplemental scripts, including the ability to replace a withdrawal 2FA authorization request with a new device authorization request within the Gmail client. This is designed to bypass 2FA when compromising a victim’s crypto account.

Prevention Methods
- Protect individual users by educating them on vigilant installation practices, employing the principle of least privilege, and continuously monitor extension updates.
- For larger organizations, consider implementing a managed browsing environment, applying strict Allowlist and Denylist policies via Group Policy Objects.
- Isolate extensions and execute, if needed, to confirm legitimacy and lack of malicious code.
Leave a comment